Introduction
While the previous versions of this website were also self-hosted the complexity has gone up drastically. When hosting your own website you have to be really careful to not let any attacker into your home network. While a lot of precautions were taken to self-host this website, there is a good chance I will put this whole system onto a VM with some cloud provider. Because if something should happen to it, it is better if it happens there instead of having a malicious machine in my own network.
Setup
For security reasons, the whole setup is not directly run on a machine inside the network but it is run inside a VM so that if something were to happen I could just delete it. Inside this VM I run the webservers as docker containers to further separate the hosted website from the rest of my setup. The docker containers are only able to talk to the internet and each other but are prohibited by the firewall from directly communicating with the home network. So that if the webserver would be compromised it couldn’t access the home network. The docker setup is split into 2 parts each containing 2 containers. On one side there are 2 WordPress containers one hosting the web server and one hosting the database. The other part is a reverse proxy that handles the SSL termination and a Certbot container that handles acquiring and renewing the certificates. The reverse proxy is just an additional layer of separation and is also simpler if I would host multiple websites since I could handle all the certificates centrally at the reverse proxy. It is also able to secure applications that would only support HTTP on their own. In my case, the reverse proxy also helps with doing access control to the WordPress docker allowing me to restrict access to things like the admin portal or the login page.
Further Security
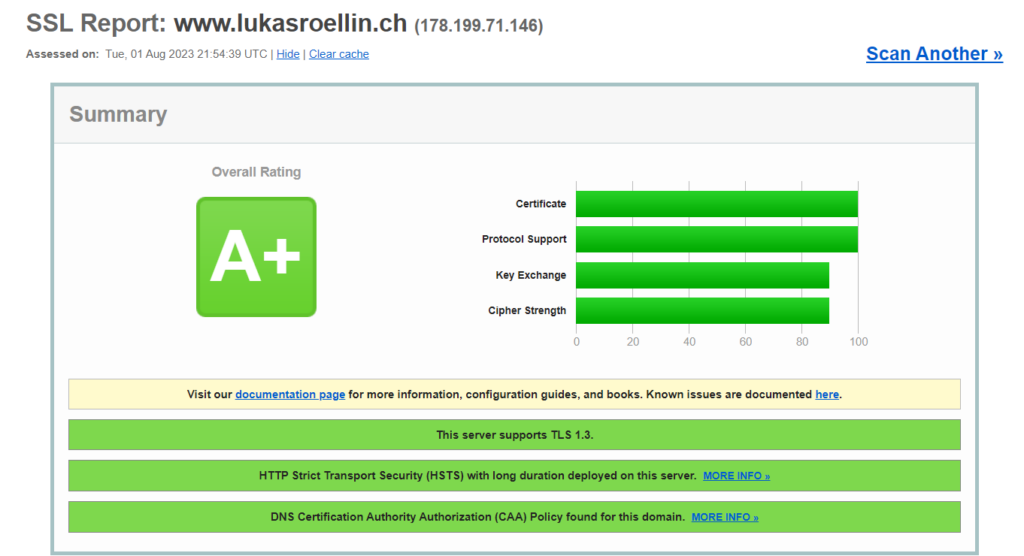
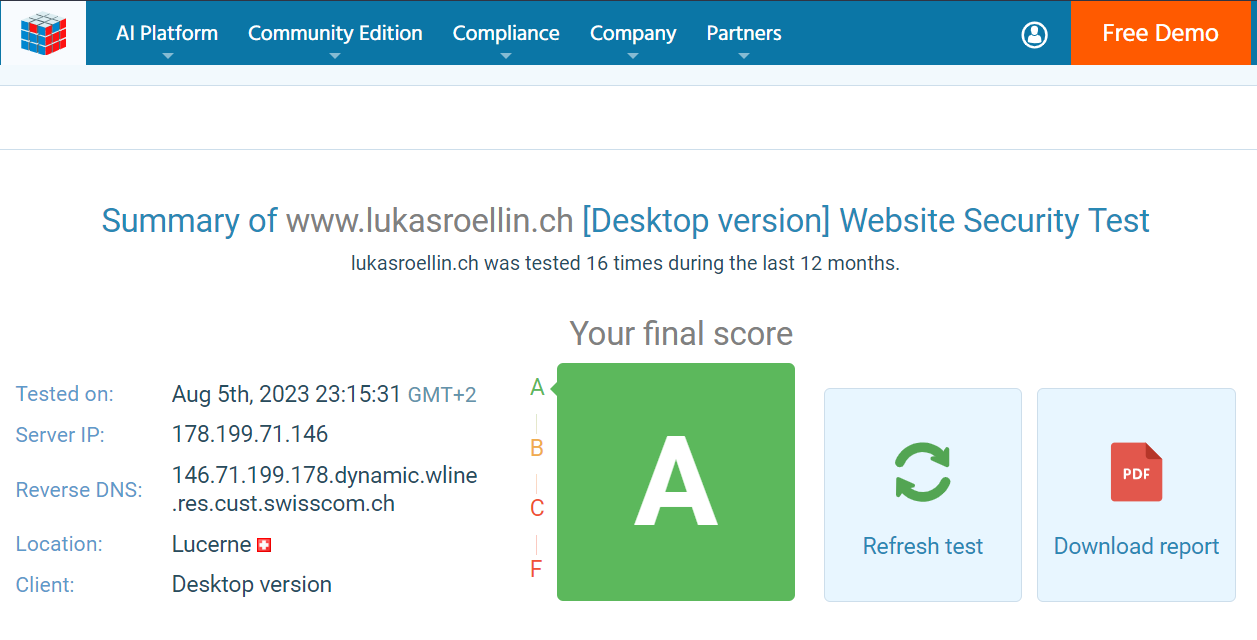
Since setting up the webpage I was already able to see attacks where malicious users or more likely automated bots tried to guess the admin password. To make it more secure I completely disabled the access to both the admin portal and the login page from the internet. If anyone should be able to get around this I still have a second layer of defense in the Sucuri WordPress plugin which is used to harden the security of WordPress websites. This plugin allowed me to see those attempted attacks in the first place. The plugin has some interesting functionality, like notifying me via email if a brute force attack is in progress. But it can also be used to keep track of unexpected changes to WordPress files and enables some automated hardening. Additionally to just trusting this setup I also started using online tools that scan the website for any misconfigurations and attack surfaces. Leaving everything in its standard configuration gave me pretty bad results. But through improving the security of the site I was able to get much higher scores.